Netflix Tech Blog: Escrow Buddy: An open-source tool from Netflix for remediation of missing FileVault keys in MDM Netflix 技术博客:Escrow Buddy:Netflix 推出的一款开源工具,用于修复 MDM 中缺失的 FileVault 密钥 Elliot Jordan: Escrowing new FileVault keys to MDM without password prompts Elliot Jordan:将新的 FileVault 密钥托管到 MDM,无需密码提示
Perhaps the Mac was encrypted prior to enrollment. 也许 Mac 在注册之前已加密。 The Mac was encrypted prior to the FileVault redirection profile installation. Mac 在安装 FileVault 重定向描述文件之前已加密。 The original recovery key was lost for some reason (e.g. database corruption or a bug of some kind). 原始恢复密钥由于某种原因(例如数据库损坏或某种错误)而丢失。
A configuration profile ensures that all FileVault keys are escrowed with the JSS. 配置文件可确保所有 FileVault 密钥都托管在 JSS 中。 A smart group determines which computers lack valid individual recovery keys. 智能组确定哪些计算机缺少有效的单个恢复密钥。 Customize the reissue_filevault_recovery_key.sh
for your environment. 为您的环境自定义reissue_filevault_recovery_key.sh。 Create a policy that deploys the reissue_filevault_recovery_key.sh
script to the computers in the smart group. 创建一个策略,将 reissue_filevault_recovery_key.sh 脚本部署到智能组中的计算机。
General Distribution Method: Install Automatically
分发方式:自动安装 Level: Computer Level
级别:计算机级别 FileVault Recovery Key Redirection Automatically redirect recovery keys to the JSS 自动将恢复密钥重定向到 JSS Scope All computers 所有计算机
| 30 | |||
Start by customizing the reissue_filevault_recovery_key.sh script as needed for your environment. Email
affected employees to give them a heads up. 向受影响的员工发送电子邮件以提醒他们。 Use jamfHelper
to announce the upcoming password prompt. 使用 jamfHelper 宣布即将出现的密码提示。 Add logo
to AppleScript password prompt. 将徽标添加到 AppleScript 密码提示中。 Fail silently
if logo files aren’t present, or any other problems detected. 如果徽标文件不存在或检测到任何其他问题,则会静默失败。 Verify
the Mac login password, with 5 chances to enter correct password. 验证Mac登录密码,有5次机会输入正确密码。
General Trigger: Recurring Check-In
触发因素:定期签到 Execution Frequency: Once per computer
执行频率:每台计算机一次 Packages AppleScriptCustomIcon.dmg
(loads /tmp/Pinterest.icns) AppleScriptCustomIcon.dmg(加载/tmp/Pinterest.icns) Scripts reissue_filevault_recovery_key.sh
(priority: After
) reissue_filevault_recovery_key.sh(优先级:之后) Scope Smart Group: FileVault encryption key is invalid or unknown
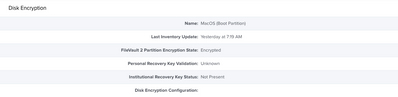
智能组:FileVault 加密密钥无效或未知
Monitor logs and flush one-off errors. (Unable to connect to distribution point, no user logged in, etc.) 监视日志并清除一次性错误。 (无法连接到分发点、没有用户登录等) Identify and resolve remaining problems manually. 手动识别并解决剩余问题。 Test a few newly-generated FileVault keys to ensure they are working as expected. 测试一些新生成的 FileVault 密钥以确保它们按预期工作。 Update your internal documentation. 更新您的内部文档。
On specific versions of High Sierra, entering an incorrect password during the key rotation process can result in invalidation of the existing FileVault key. Since the existing FileVault key is not valid in the first place (presumably) this isn't the end of the world. But it means that if the key was stored separately, e.g. in a spreadsheet somewhere, it will no longer work. 由于现有的 FileVault 密钥一开始就无效(大概),这并不是世界末日。但这意味着如果密钥是单独存储的,例如在某处的电子表格中,它将不再起作用。 We attempt to mitigate this by validating the provided password with dsclprior to using it for rotation of the FileVault key. However, there is no guarantee that your local account password and your FileVault password are the same. 我们尝试通过在使用所提供的密码进行 FileVault 密钥轮换之前使用 dscl验证所提供的密码来缓解此问题。但是,不能保证您的本地帐户密码和 FileVault 密码相同。Previous versions of macOS generated log output that confirmed the successful escrow of the newly generated FileVault key. High Sierra and Mojave do not. Instead, a local file containing the new key is written, which MDM is meant to retrieve. We attempt to determine escrow success by detecting a change in that file, but it's not a guarantee of success. 以前版本的 macOS 生成的日志输出确认新生成的 FileVault 密钥已成功托管。高山脉和莫哈韦没有。相反,会写入包含新密钥的本地文件,MDM 会检索该文件。我们尝试通过检测该文件中的更改来确定托管是否成功,但这并不能保证成功。 If you find additional issues with High Sierra or Mojave, I'd appreciate you on this repo. 如果您发现 High Sierra 或 Mojave 的其他问题,我将不胜感激您在此存储库上提出问题。